A few years before this write-up, I had a major security issue with my portable router. The router provided a web app and a mobile app for management, however, I found a vulnerability that enabled one to exploit its REST API to get admin privileges. What if I could patch that? This is the question that sparked curiosity about router firmware.
Router firmware is software used for the overall operations of the device - from networking to management - you name it.
I am glad to share how you can explore firmware and understand it grain by grain.
Preface
At the end of this article, you will know:
Basics about firmware.
Downloading firmware.
Exploring the firmware bin file.
Extracting the compressed file system.
Understanding the filesystem.
Prerequisites
To get the best out of this, please have the following:
- Linux (Any distro)
Getting started
To begin with, we need a firmware file to play around with. While you can interface with your router motherboard's UART controller to get the firmware directly from it, this process is tedious and involves a lot of prayers and the casting of curse words.
Well, an easy way of getting the firmware is by downloading it from the internet. Type your device's model number on Google search like so.
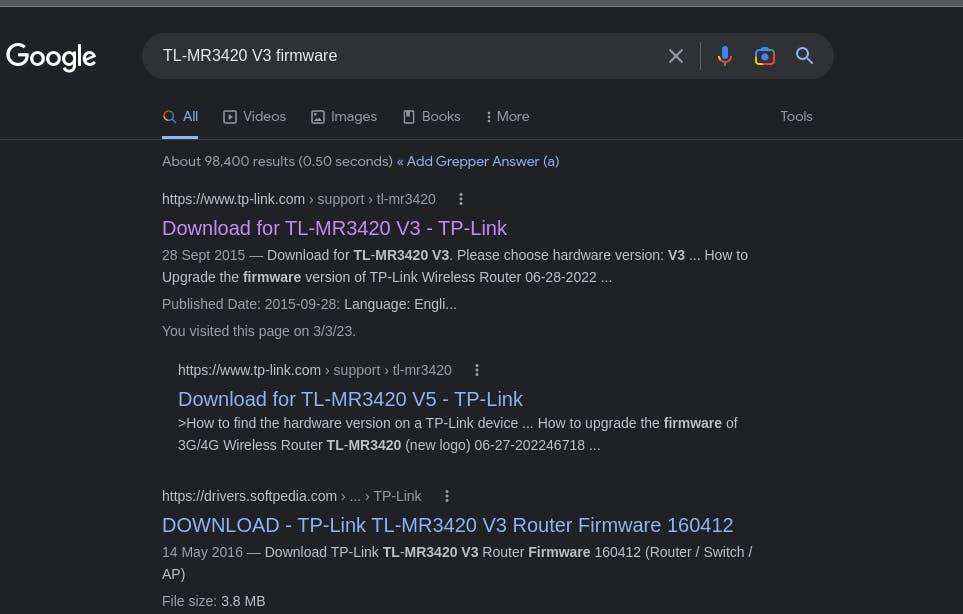
Click the appropriate links that will lead to getting the right firmware file for your device.
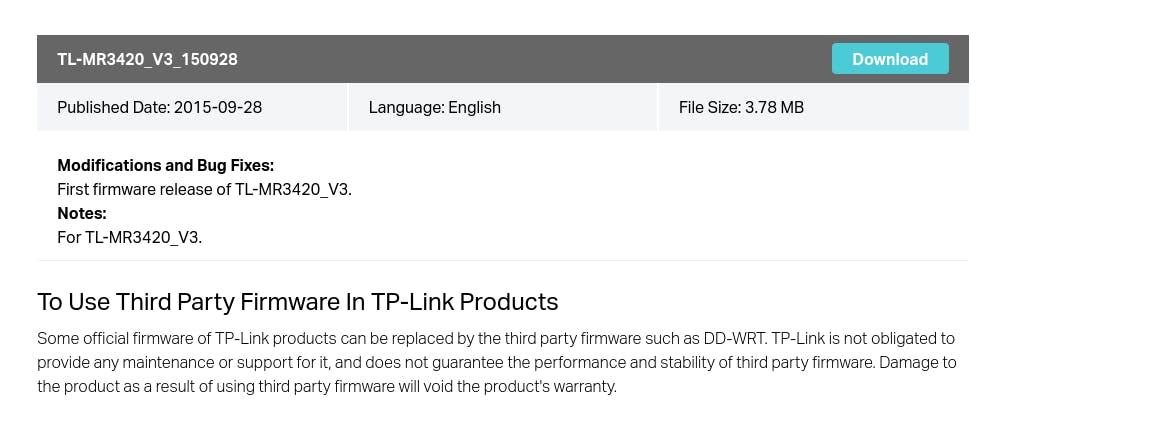
In this article, I will be using the router mentioned above. It is a 32-bit MIPS-based router. It is pretty basic and fit for learning purposes.
With the download done, it's time to explore the binary file.
Exploring the firmware
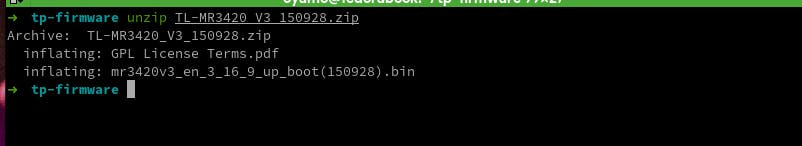
To start with, let's extract the zip file that contains the binary file.
unzip TL-MR3420_V3_150928.zip
A pdf file and .bin file will be created in the current directory. You will get an output equivalent to this .
Right now, there lies a mysterious file `mr3420v3_en_3_16_9_up_boot(150928).bin`. It is just a collection of bytes. Binwalk is an awesome tool for exploring binary files, It is used for searching for embedded files and executable code
You can get it using any of the following commands depending on your file system.
# Fedora/ centos
sudo dnf install binwalk
# Ubuntu, Debian, Kali
sudo apt-get update && sudo apt-get install binwalk
Time to 'walk over' the binary file.
binwalk mr3420v3_en_3_16_9_up_boot(150928).bin
After a few seconds, this will fill up your terminal.
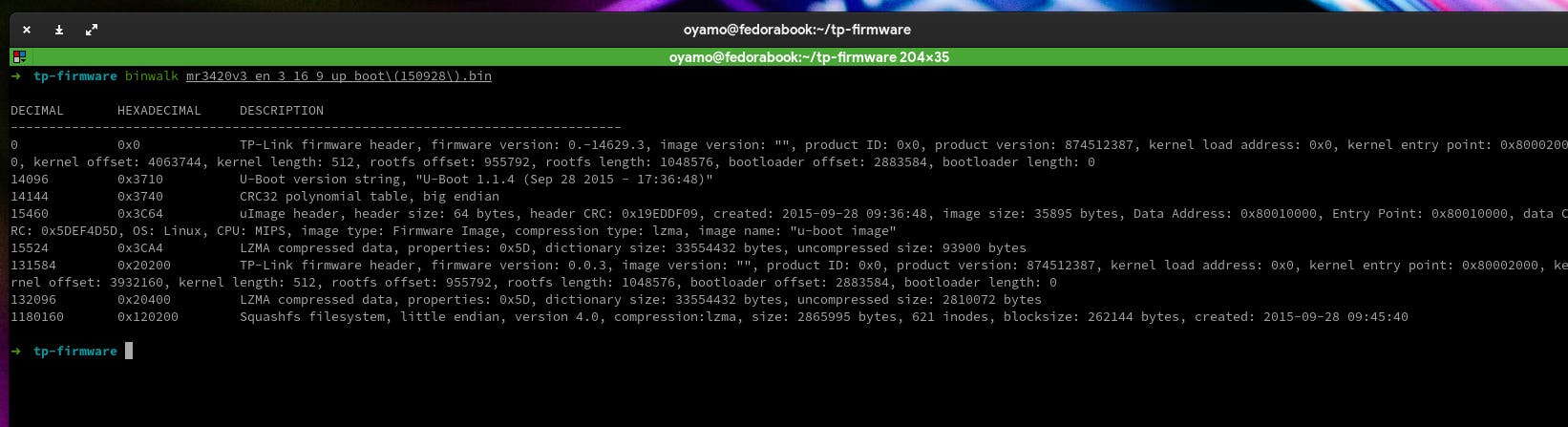
The output is made up of several sections. Do not fret, I will explain everything in details.
TP-Link firmware header (offset 0): This section contains information about the firmware image, such as the firmware version, product ID, and kernel load address.
U-Boot version string (offset 14096): This section identifies the version of the bootloader used by the device.
CRC32 polynomial table (offset 14144): This section contains a table used to calculate CRC32 checksums.
uImage header (offset 15460): This section is a header for a type of image format used for bootloaders and kernels on some embedded systems. It includes information such as the image size, data address, entry point, and compression type.
LZMA compressed data (offset 15524): This section contains data that has been compressed using the LZMA algorithm. This could be an executable, a kernel, or some other type of data.
Squashfs filesystem (offset 1180160): This section is a compressed read-only file system often used in embedded systems such as routers. The filesystem contains various files and directories that make up the operating system running on the router.
We are interested in the bytes found in the last section. Squashfs is a filesystem mostly used in small devices. When we decode this file system, we will be able to see the software that powers up the router.
Let us start by extracting the filesystem from the binary file.
dd if=mr3420v3_en_3_16_9_up_boot\(150928\).bin skip=1180160 bs=1 count=2865995 of=mystery.image
The dd command extracts a section of data from mr3420v3_en_3_16_9_up_boot(150928).bin starting at byte offset 1180160 and saves it as mystery.image.
if: specifies the input file (in this case,mr3420v3_en_3_16_9_up_boot(150928).bin).skip: skips a specified number of bytes at the beginning of the input file before starting to read data.bs: sets the block size used for reading data from the input file.count: specifies the number of blocks to read from the input file.of: specifies the output file to write the extracted data to (in this case,mystery.image).
Our center of interest is now shifted towards mystery.image. It's quite a mystery, but only for a while, it is only a matter of time.
As we mentioned, it is a filesystem image. We can choose to mount it or just extract the contents using unsquashfs tool. Well, we choose the latter.
sudo unsquashfs mystery.image
The files inside the file system will be written into out local folder. You will get an output that is similar to this.
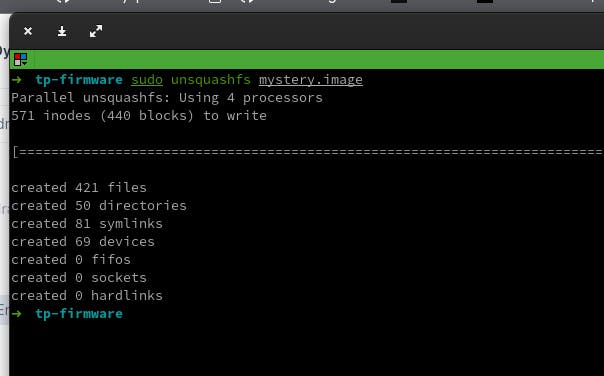
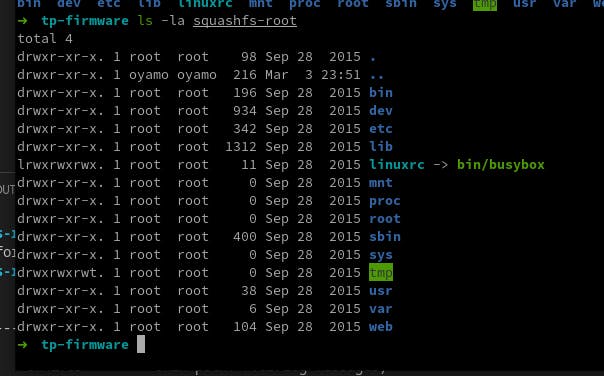
Exploring the extracted files.
Here is where the real adventure begins. You can browse over the files for your understanding. Whatever you can do with this is boundless, only limited by your imagination.
The first conclusion we can make about this firmware is that it uses a Linux kernel and is probably running as Busybox Operating system.
The front-end part of the management dashboard is stored in the
/web/folder.The executables are compiled for MIPS architecture.
The router's flash storage is in
/dev/sda
I hope you found this useful. Onto the next device!!